Tunneling Web Traffic Via SSH
If you familiar with Linux and Unix environments you might be aware of SSH. In addition to connecting securely to the Unix machines via SSH, you can also tunnel all your web traffic via remote machine.
There are many SSH clients available for windows but, I will be demonstrating using PuTTY.
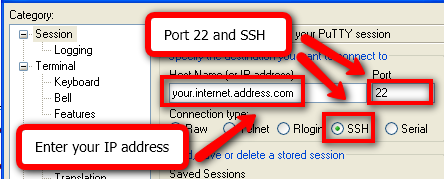
First, specify the address of your SSH server in the Session section. Select SSH for the Connection type and enter 22 for the Port (or whatever external internet port you are using to connect to your SSH server).
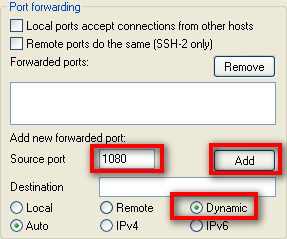
Next, go to Connection > SSH > Tunnels. There are three types of tunnels you can set up. For connecting to a UniX server with public IP, select Dynamic as the port type. et’s first set up a dynamic tunnel for port 1080. The port you use for a dynamic tunnel is actually arbitrary, but since port 1080 is often used for SOCKS proxies that’s what we’ll use. Type 1080 in the Source port field, select Dynamic as the port type, and then click the Add button.
Once you have everything configured for the connection, go back to the Session section and save your connection. Then click Open and log into your Linux box with your credentials as you normally would.
Now you have to configure your applications to use the tunnels you have set up. Let’s say you want to do your web browsing through the dynamic tunnel we set up. This is actually an extremely useful way to take advantage of SSH.
You may be on a network with some sort of firewall or content filtering that you wish to bypass. If you are able to get out on port 22 (or any other port, you’ll just have to set up your SSH server accordingly), then you’ll be able to surf wherever you want without issue through the dynamic tunnel.
It is also useful if you are surfing on a network where you may be concerned about others observing your traffic. Perhaps you are connecting from a hotel, a client site, or from work (you didn’t learn that from me) and you do not want others monitoring your traffic.
The best choice is to use Firefox, because Firefox allows you to configure the browser to also send DNS requests through the proxy. If you use Internet Explorer, your DNS requests are still made via the local network you connect from and thus can still be monitored. So Firefox would be the preferred browser if you wish to maintain privacy on the network you are connecting from.
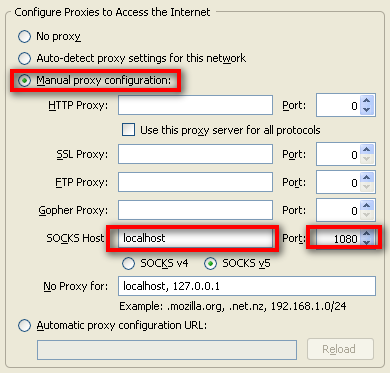
To set up Firefox to use the dynamic tunnel as a SOCKS proxy, go to the Firefox Options > Advanced > Network and click the Settings… button. In the settings page, click Manual proxy configuration, enter localhost for the SOCKS Host, and 1080 for the Port.
We’re not quite done. We still need to configure Firefox to send DNS requests to the SOCKS proxy as well. To do this, enter about:config in the navigation bar in Firefox. You may get a prompt asking you if you know what you’re doing. Assure Firefox that you know what you’re doing and proceed.
Enter socks_remote_dns for the Filter and press enter. You should see a single option that says network.proxy.socks_remote_dns. If it says false for the Value, double-click on it so that it says true. You’re now all set. You should be able to surf the web through your new secure dynamic tunnel!
Source: http://www.makeuseof.com/tag/how-to-tunnel-traffic-with-ssh/




Leave a Reply